
Alicia Asín – June 20, 2008
First steps for securing a Meshlium.
- Change root password (user)
- Change root password (Manager System)
- Hide ESSID rolex daytona 116568 40mm mens oyster bracelet automatic bv factory
- Select encryption method
- Enable MAC filtering
- Protect OLSR traffic
- Protect data inside the Meshlium
- Backup configuration
- Change root password (user)
First of all, change the default root password of the router by opening a ssh session. If you have a cross link you do not need to connect the router to the network but your computer. ali@kaizen:~$ ssh [email protected]
[email protected]’s password: Once logged, change the password: meshLium-AX:~# passwd
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
- Change root password (Manager System)
Secondly, change the default root password for accessing the Meshlium Manager System (manage tab). Preferably, do not use the same root password as the root user of the router.

Hide ESSID
When configuring an AP it may be interested to hide the ESSID.

This makes the AP partially unvisible so that only clients who know the ESSID can associate to it. Clients who scan the network will get something like this:
root@kaizen:# iwlist eth1 scan
Cell 10 - Address: 00:0B:6B:80:C8:8E
ESSID:""
Protocol:IEEE 802.11bg
Mode:Master
Channel:1
Encryption key:on
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s 9 Mb/s; 12 Mb/s; 18 Mb/s; 24 Mb/s; 36 Mb/s ; 48 Mb/s; 54 Mb/s
Quality=59/100 Signal level=-72 dBm Noise level=-72 dBm
Extra: Last beacon: 1636ms ago
- Unfortunately, this method can be avoided using some network analyzers, like kismet, so the security of the AP must not rely in hiding its ESSID, as we can see in the following picture:

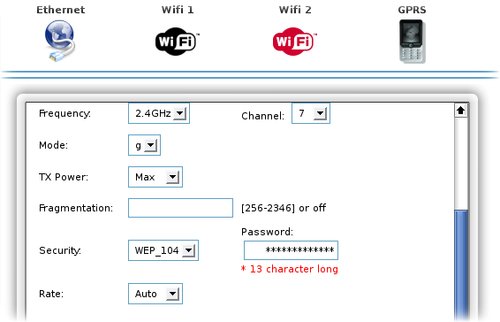
- Select encryption method
For encrypting the traffic between clients and the Meshlium AP, an encryption method must be configured. For the moment, Meshlium supports WEP40 (5 characters password), WEP 104 (13 characters password) and WPA-PSK (8-63 characters password). When configuring them through the Meshlium Manager System all of them use authentication in open mode, this allows all clients to associate to the AP without demonstrate they know the WEP key. This authentication method is safer than the shared, since it uses the SSID in the process, so everyone could see it and use it to decrypt the encrypted message and get the WEP key.
- Enable MAC filtering
If controlling the clients who can associate to the AP is desired, it can be activated the MAC filter. If the blacklist policy is chosem MACs in the list will be banned automatically On the contrary, if the whitelist is chosen only MACs specified will be allow to connect to the AP.

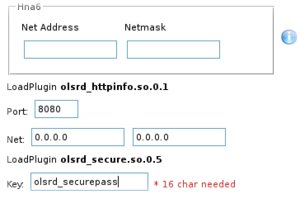
- Protect OLSR traffic
If the Meshlium used is a mesh one, an extension to secure OLSR can be activated. Important! This extension only provides security extensions to OLSR and not the traffic being routed in the MANET. Also, the implemented solution only provides integrity and not confidentiality, although the solution is extendable and could include mechanisms to provide confidentiality. More info in this link. Encrypting all the traffic in the networks requires other solutions like SSH tunneling, which will be covered in future articles.
- Protect data inside the Meshlium
The information stored in a node of a computer network may be critical in some cases: accountancy files, medical or student’s records, customer data bases, log and config files, data acquired from a sensor network or even executables. Having this data encrypted prevent them from being unveiled if the router where they are stored is stolen. Only those who know the encryption password would be able to access the data, minimizing the damages. If you are responsible of critical information stored in the network nodes of your customers you should consider protecting these data. There are many solutions to keep files safe, either ciphering them separately or putting them in an encrypted partition protected with a password. The Meshlium Manager System provides a mechanism for creating easily an encrypted partition to store data. When the partition is created, you can save files directly and keep them ciphered. Whenever the router is powered off, the encryptied partition must be activated by entering the password. This ensures that the information will not be legible in case someone steals the router. Once the partition is activated, it is accessed through a mapper which encrypts or decrypts on the fly the data written and read from the partition so that the data always remain encrypted. Accessing to these data without the encryption password is impossible, even knowing the root machine password. Step a step info about this process in this link. More info about the use of the encrypted partition in this article.


- Backup configuration
Finally, after configuring your Meshlium it is important to backup the configuration so that you can rescue it in case you need to reset the router to an older configuration. This feature can be also used for replicate fastly the configuration of one Meshlium to the rest of the routers in the network.







